Leveraging Modern Infrastructure for Next - Generation Threat Intelligence

TABLE OF CONTENTS
Need Help ?
Our team of experts is ready to assist you with your integration.
Introduction to Threat Intelligence Companies
Threat Intelligence is a crucial part of cybersecurity, helping organizations stay ahead of digital threats by constantly identifying, analyzing, and alerting on potential breaches. Without them, breaches may go unnoticed, putting not only individual businesses but the entire internet ecosystem at risk. From banking to healthcare, trust in digital systems hinges on timely and effective threat detection.
But as cyber threats evolve rapidly, the challenge is no longer just about having the right data but about getting that data faster and more efficiently. Threat intelligence providers are under immense pressure to deliver insights in real time. And in this high-stakes environment, even a few seconds of latency can slow down detection, investigation, and response. Consider the example of July 2024, when CrowdStrike, one of the most deployed threat intel feeds rolled out a bugged update to its Falcon Sensor on global Windows platforms, crashing millions of endpoints worldwide, freezing business, banks, hospitals, and carriers. It all started with a busted detection rule in a kernel-mode data file.
It's not uncommon for teams to compromise on thoroughness to avoid long query wait times or infrastructure bottlenecks. In many organizations today, analysts deliberately limit the number or depth of queries not because they lack data, but because existing search infrastructure simply can’t handle the load efficiently or affordably.
In this blog, we’ll explore how the threat intelligence space is evolving, the operational challenges companies are currently facing, and the critical infrastructure shifts needed to keep up. From real-time data demands to the rise of AI-driven detection, we’ll look at what’s holding teams back and what it takes to stay ahead in a rapidly changing threat landscape.
Rethinking the Role of Threat Intelligence Infrastructure
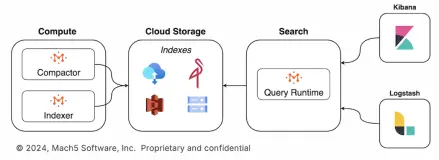
Traditional threat intelligence platforms are essentially sophisticated search engines that are indexing massive volumes of cybersecurity data across various sources. But the real challenge is not just searching, it's searching fast and often.
Today’s versions of OpenSearch/ElasticSearch have been retrofitted with “auto-scaling” functionality, but as anyone who’s tried setting it up knows, it requires deep expertise in the product to configure node roles and IS/LM correctly and introduces costly, on-going maintenance and complexity.
For example, security analysts often know what they are looking for—be it threat indicators, IP reputation, behavior over time or something else—but if querying a million records takes too long or costs too much, they’re forced to cut corners. Inaccuracy in detection might not always be due to bad data, but due to insufficient querying.
This constraint doesn’t just affect humans. It’s even more limiting with the rise of AI agents. Unlike static SIEM queries, AI agents are now executing millions of dynamic queries in real time to uncover threats, automate responses, and support SOC teams. And the only thing holding them back is the speed and scalability of the underlying search infrastructure.
The ability to perform high-volume, real-time searches across massive datasets is becoming a defining factor in how well organizations can respond to threats. This is especially true as modern security operations shift from static detection rules to dynamic, high-frequency querying that’s driven not only by analysts, but increasingly by automated systems and AI agents.
Challenges with Traditional Search Infrastructures
Most threat intelligence companies today still rely on legacy search infrastructures like Elasticsearch and OpenSearch. While initially effective, these platforms increasingly present critical operational challenges to threat intelligence companies across the globe:
Scalability Issues
Conventional infrastructure does not scale well with fluctuating data loads, usually requiring intervention by hand. It causes bottlenecks, instability, and reduced functionality.
Performance Inconsistency
At high load utilization, unpredictable query times greatly affect service-level agreements (SLAs) and undermine client trust. Referring again to the CrowdStrike use case, it ran for around 13 hours before remediation and created real anxiety among the security team relying on real-time threat detection for prevention of threats. Whilst no breach occurred, the delayed threat detection and sluggish response eroded client trust and proved that inconsistent performance, even for an instant, can be detrimental to SLAs as well as reputations.
Data Latency
Sluggish data ingestion and gradual processing hamper rapid threat detection and response, making it impossible for Threat Intelligence companies to provide real-time insights.
Complex Operating Management
Productive engineering resources are spent on time-consuming manual tuning work and maintenance, diverting attention away from strategic innovation and customer work.
Limited Resilience
It is difficult to achieve strong global availability with predictable multi-region data synchronisation, resulting in frequent service disruptions and operational inefficiencies.
Poor Fit for AI Agents
Traditional search systems can't handle the high-frequency, concurrent queries AI agents require, creating performance bottlenecks that limit automation and slow down threat response. As AI becomes central to modern SOC workflows, this limitation increasingly hampers scalability and efficiency.
How Mach5 Addresses Modern Threat Intel Demands
While Mach5 doesn’t fix broken threat feeds or prevent flawed detections, it does solve issues seen with traditional search systems like speed, scale, and efficiency of search. Whether you're an analyst running 1,000 queries or have built an AI agent executing a million of these, Mach5 ensures you get the results fast and cost-effectively.
Optimized Infrastructure Costs
Mach5 significantly cuts down infrastructure expenditures by streamlining resource utilization and eliminating extensive manual maintenance tasks. This translates directly into improved ROI, allowing threat intelligence companies to reinvest in strategic growth and customer innovation.
Effortless Scalability for Peak Loads
Mach5 manages increasing data ingestion, compaction, and query demands without requiring complex manual configurations. Its simplified approach guarantees consistent performance, reducing operational complexity even during periods of intense data activity.
Robust Multi - Region Replication
Mach5 enables easy replication and synchronization across multiple AWS regions, ensuring enhanced system reliability, availability, and global operational resilience, overcoming the limitations typically associated with traditional search systems.
Real - Time Query Performance
Mach5 consistently delivers rapid and reliable query responses with sub-second latency, effectively meeting stringent SLAs and reinforcing client trust. Its robust architecture handles high concurrency effortlessly, removing the unpredictability associated with legacy solutions.
Seamless Real - Time Data Integration
Mach5’s built-in Kafka integration allows real-time streaming and updates to threat intelligence reports. This ensures immediate data freshness and accuracy, significantly accelerating the delivery of critical insights and enabling faster response to emerging threats.
Operational Comparison : Traditional Search vs Mach5
| Operational Aspect | Traditional Search | Mach5 Search |
|---|---|---|
| Performance | Unpredictable under load | Consistent sub - second response at scale |
| Operational Complexity | Frequent manual tuning | Auto - scaling and zero - touch configuration |
| Cost of Ownership | High compute + storage spend | Split architecture reduces TCO and improves ROI |
| Scalability & Stability | Fragile and hard to extend | Elastic scaling with object storage and no downtime risk |
Conclusion
Threat intelligence isn’t just about having the data, it’s about accessing it when it matters most. As cybersecurity shifts toward automation and real-time AI agents, the underlying search infrastructure must evolve too.
Mach5 was purpose-built for this next generation of threat intelligence—enabling lightning-fast access to massive data sets, without compromising on scale or cost. It helps companies spend less time managing infrastructure and more time investigating threats.